After a while searching for an older version of an App from the Play Store, I finally found the version I wanted and downloaded it.
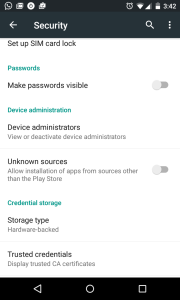
In order to install it, you have to “Allow the installation from unknown sources”. So there goes the chain of trust for the app.
So how do you know:
- Where did the app came from ?
- Did someone plant Malware in it?
- Can I trust it?
These are cases for your trusted cryptographer or in the case your certificates.
Basically you need fo follow these steps:
# Dump the apk information $ANDROID_HOME/build-tools/23.0.0_rc2/aapt dump badging www.apks.org-de.hafas.android.db.apk |grep package # verify the signer jarsigner -verbose -verify www.apks.org-de.hafas.android.db.apk |less
# Verify that all files have been signed with the same key jarsigner -verbose -certs -verify www.apks.org-de.hafas.android.db.apk |less