
This was my second BSides event of this year. I must say I really like this type of events and I hope I can attend more of them next year. I don’t think I can cover as many as Cooper (@ministrator), but I would love to.
For those of you who haven’t attended one before I ‘ll run you through the basics. Community organized, very nice people, great content (normally delivered by non Rockstar speakers) and non-profit.
Every BSides event has their own twist, and in the case of the BSide Lux it was all about playing defense or blue teaming. This was a really great change of pace for me, because the last couple of years I’ve focused on offence and testing of IoT. It was a refresher on the techniques and technologies used by defenders. This year there was a big trend on Elastistack or ELK.
There were two rooms so I could not attend all the talks. But they were all recorded so I can catch up with the ones I missed.
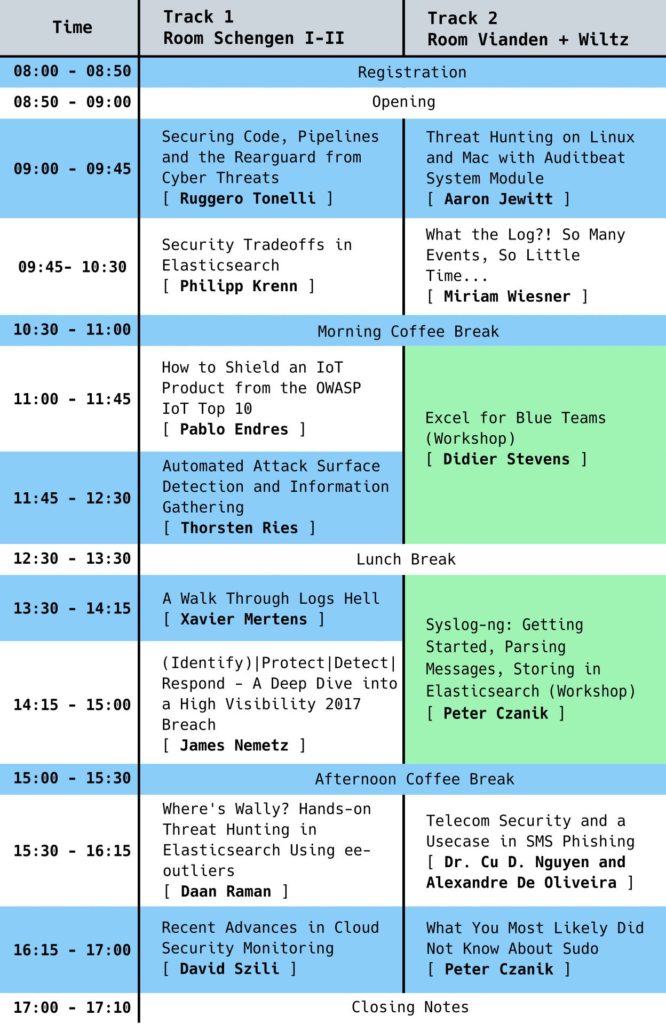
Here are the highlights of the talks where I feel I took the most with me home:
Miriam Wiesner (@MiriamXyra), showed us how to create rules on Windows to log the things you really need and try to tune off the rest. It is impressive the amount of material she had to shift through to create her tool Eventlist.
Thorsten Ries, shared what he and his team are doing to do “Automated Attack Surface Detection and Information Gathering”. The summary of the methodology would be:
Scan > Enrich > Report > Mitigate. It is still “work in progress”, hopefully he will be able to share the system as open source once it reaches a certain maturity.
Xavier Mertens (@xme), did a great job sharing his experience with managing logs and incidents based on them. A handful of the do’s and don’ts that are really worth remembering.
James Nemetz, shared his analysis of the Equifax breach. He had the patience and nerves to review congressional sessions and all the papers published about it. It was a great session of lessons learned or at least we should hope everyone should learn from. It also confirmed that these major breaches are never the result of just one mistake but rather a long tail of technical and organizational mistakes.
Daan Raman (@daanraman) shared a model / framework used to detect statistical outliers. It was really cool how with simple models they could actually identify the attacks in a mound full of logs. The tools can be found here.
Peter Czanik (@PCzanik) showed lots of uses you probably you didn’t know about sudo, including requiring the approval from a second person to run a command and sessions recording. The latter is great for those cases where you need to grant access for support.
I cannot close this piece without thanking the organizers and volunteers for running a great event. They also gave me the chance to speak about IoT Security with my talk “How to Shield an IoT product from the OWASP IoT Top-10”

I had a great time and learned a lot. Caught up with old friends and made new ones (all in a little more than a day) I’m looking forward to see you again next year.
PS: I took home some SWAG:


Recent comments