Even though a don’t agree with many of the decisions and laws created in Venezuela, I think this is great example of implementing a control for a big risk. Keep Reading →
Ubuntu Firefox: This address is restricted
I got the weirdest of errors today trying to open a web page on port 6000: 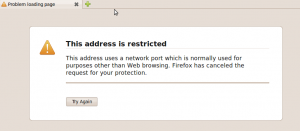
After reading for a while I found out that de Mozilla Foundation built in this protection for “Cross-Protocol” scripting attack with a form of Port Banning.
To overide this protection use one of the following steps:
- In the user’s profile directory the all.js, add the following line at the end of the file
user_pref("network.security.ports.banned.override", "1-65535"); - In the defaults/pref/ sub-directory of the installation directory (multi-user systems) add the following line at the end of the file
user_pref("network.security.ports.banned.override","1-65535"); - Open a new window, in the address type: about:config and add a new entry of the type string with this name network.security.ports.banned.override and value 1-65535.
If you want to set free only one port change the range for that port o list of ports.
US Access to SWIFT data
This is a topic that caught my eye a while ago and just found out it’s still an open issue.
According to their website:
SWIFT is the Society for Worldwide Interbank Financial Telecommunication, a member-owned cooperative through which the financial world conducts its business operations with speed, certainty and confidence. Over 8,300 banking organisations, securities institutions and corporate customers in more than 208 countries trust us every day to exchange millions of standardised financial messages.
So basically it’s the organization that manages the API’s and systems that make international banking work smoothly.
This Belgium based organization had it’s major databases in the US until an article in the NY Times aired that the CIA under the Bush administration had been data mining the database to find links to terrorism, after Europe protested the database was move to Holland. So the issue now is that the US intelligence agencies want to keep having unlimited access to spy on EU Citizens using the usual terrorism joker card.
I think this is a big issue and should be handled a such. There are some open questions I have to this deal:
What does a US or in fact any intelligence agency have to do with our financial records without a warrant?
Is every person in the world considered a potential terrorist?
Were are rights, are privacy?
While we’re at it: How long is this data retained? How is it guarded? Who makes sure it’s correctly discarded?
Benjamin Franklin summed this up better than I can ever try to:
They that can give up essential liberty to obtain a little temporary safety deserve neither liberty nor safety
Creating passwords with bash + perl
I had a couple of scripts working in the back end of an application to create users and set the passwords. So instead of reinventing the wheel I used the ?trusty? useradd.
Until recently one could pass the users password in clear text as a parameter. I assume that someone thought about all the passwords that word saved in history files and decided to change it. The problem is that the used the same parameter but now it expected the password to be encrypted, so it basically stopped working but didn’t generate errors.
After some debugging and some man reading the problem was nailed down, but now I had to generate and encrypt the password. I looked and tried many solutions but the best I could find was the crypt library and decided to access is through perl. What I liked the most about the solution is that I could use all the same native algorithms that the system has installed.
So lets cut the chase, here are the 5 lines of code needed to get the job done:
salt=$(/usr/bin/mkpasswd -l 8 -s 0)
parameter=”print crypt(config,”\$1\$$salt”)”
encrypted=$(perl -e “$parameter”)
/usr/sbin/useradd -p $encrypted <user>
To create a good salt I used the mkpasswd utility that comes with the expect package (yum install expect). In this case the $1 is not a variable, but the way of telling crypt to use MD5.
Other valid values for the Glibc crypt are:
| ID | Method |
|---|---|
| 1 | MD5 |
| 2a | Blowfish (not in mainline glibc; added in some Linux distributions) |
| 5 | SHA-256 (since glibc 2.7) |
| 6 | SHA-512 (since glibc 2.7) |
For more information http://www.kernel.org/doc/man-pages/online/pages/man3/crypt.3.html or simply: man crypt
Have fun
ISECOM TtT
I managed to get a few days away from the day job to attend the ISECOM Train the Trainer event in Barcelona (27-29 May) and it was really a great experience. Being that the event was for the certified or to be certified trainer crowd it was pretty intense and at the end of the last day my brain was jello.

Jello Brain
It was great to finally meet Pete Herzog, who I had the pleasure of working with before on the Hacking Expossed book. I also got time to meet some of other European trainers, and it’s a good batch 😉
I got to take the OPSA and OPST exams, the results should be due any time now. I really liked the format of both cert exams: hands on! For the OPST you have to shoot at a couple of live test systems to complete the results you need, and for the OPSA there is a little theory on the OSSTM, some shooting to be done but most of all analysis (hence the A in OPSA). I fried my brain on the last question, I didn’t notice at the begining that it was a packet dump that needed to be analyzed. So after 8 hours of class the 2.5h I took to complete the exam were the last effort.
For those of you who have no idea of what I’m talking about, you can find information on the OSSTM at http://www.isecom.org/
GnomeKeyring =? ssh-agent
This feature just popped up and started working after I upgraded to Fedora 10 and I though it was a standard function in gnome, but I was working with Per the other day and his Ubuntu 8.04 didn’t have it running out of the box. So I had to take a look a the docs to make it work: http://live.gnome.org/GnomeKeyring/Ssh
This is just one of those features that make your life easier but handling all the ssh sessions for you, the best part is that is one of those setup once and forget feature. Here is a brief introduction on how it works:
According to the ssh-agent man:
ssh-agent is a program to hold private keys used for public key authenti-
cation (RSA, DSA). The idea is that ssh-agent is started in the begin-
ning of an X-session or a login session, and all other windows or pro-
grams are started as clients to the ssh-agent program. Through use of
environment variables the agent can be located and automatically used for
authentication when logging in to other machines using ssh(1).
So what gnome did was include an ssh-agent in the gnome-keyring(-daemon), so it has one interface to manage passwords, ssh keys, etc. Underneath the hood this is how it works:
- When Gnome starts the gnome-keyring-daemon (if it is enabled in your conf)
- The keyring manager starts the ssh-agent component and sets up the SSH_AUTH_SOCK variable, that will redirect ssh to make the queries to that socket
- The SSH agent automatically loads files in ~/.ssh having names starting with id_rsa or id_dsa or any other keys included by using the ssh-add command
That does the job. If you need to get it working on your Gnome installation follow the instructions here.
snmp errors in syslog
I finally got fed up of these messages in my log files (/var/log/messages) and decided to do something about them:
Apr 19 04:14:47 hostname snmpd[3458]: Connection from UDP: [127.0.0.1]:42482
Apr 19 04:14:47 hostname snmpd[3458]: Received SNMP packet(s) from UDP: [127.0.0.1]:42482
After reading, googling around and testing for a while I rounded it the following solution, it should work in any Linux system with net-snmp after some tweaks but out of the box on CentOS, REL, Fedora or any of its relatives:
1. Remove the -a from the snmpd start options or write this in the /etc/sysconfig/snmpd.options file:
OPTIONS=”-Lsd -Lf /dev/null -p /var/run/snmpd.pid”
This should take care of the “Received SNMP” packets line (2nd one).
2. Add dontLogTCPWrappersConnects true at the end of your /etc/snmp/snmpd.conf file, that takes care of the other line:
Apr 19 04:13:47 dcf-is1p snmpd[3458]: Connection from UDP: [127.0.0.1]:48911
According to the man page: This setting disables the log messages for accepted connections. Denied connections will still be logged.”
The problem is that the default settings are to log every connection / request, so what we did was leave the log work only for failed and authenticated attempts
Enjoy readable logs!
Changes to the data collection law in Germany
I’ve been living in Germany for a little more than a year now, and since then lots of things have really impressed me in the way privacy, digital rights, data collection, infomation security are managed in politics.
There have been some major attempts to create a state of surveillance protect the people and the institutions from hackers, terrorists in exchange for freedom and civil liberties. Let’s take for example the Skype Trojan they intented to create and use out in the wild without warrants, the prohibition of “hacker tools” or the data collection law.
After giving a big fight, last week the court in Karlsruhe ruled that:
Data can only be collected when the stability or security of Germany or another country need to be defended and “life, limb, and freedom of German citizens” need to be protected (The Register)
I think this is a mayor advance, and I really hope this will be followed by action in the other controversial laws.
What is X in English please!
Reading through the Red Hat Magazine I found an article with something of a Dejavu: user awareness and “education”. I’ve read it, heard it and said it a billion times; if we can’t make the users aware of the risks that they are exposed to on a daily basis, of some basic concepts, we are all screwed!. I bet all of you have lived at least once to be sitting in an class room, auditorium, web cafe or any other place and the guy or gal next to you just smacks you with the most basic of questions: What is X? in English please! That’s the moment when one of two things happen:
- You turn around and look at him with anger and think what the hell is this specimen doing attending this class/talk/presentation/name it?
- You remember about that user awareness thing you’ve read about in so many articles and books before , give him a short answer and after it’s all over you try to break this poor soul the basics
As I stated before if we can’t make the users understand a bit of how a computer works, if we can’t help are colleagues, family & friends get the basic concepts of the machine and the network they have at fingers it’s a fight we cannot win. That is because the “bad guys” are going to target them and they are just to many. So when ever you get 5 minutes to work as a multiplier, to break some basics to your users, or better yet are in position to start program in the office do so. The world and all fellow security / technology savvy people will thank you.
AV Comparisson
About a year ago I went through the process of evaluating AV’s for the company I was working for.
What I did was the following:
- Setup some detection tests using Eicar and some “wild” viruses.
- I asked some vendors that I had short-listed (Symantec, Sophos, Panda, Fortinet) to provide fully fledged versions.
- For each of the vendors I looked up their listed vulnerabilities in the past year (ovdb) and the time it took them to issue and install an update.
- Compared the upgrade strategy: engine, threat DB, application; some vendors don’t automatically give you all of that.
- Used info from http://virusbtn.com to compare some results in time.
- Setup demos to see them in action, and test their reporting capabilities in real time.
- After all the technical work, of course $$$ came into play.
With the information I made a BIG table and put some weights on the items and let the best player win.
PS: For those who will ask, Sophos came out with the best results in our environment.

